Auditing the Oral-B App (v5.0.0)

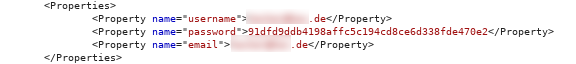
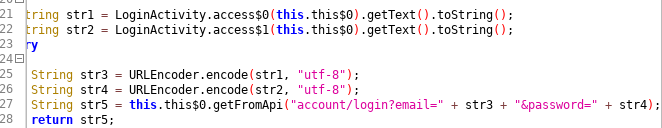
Upon quickly assessing the Oral-B app (com.pg.oralb.oralbapp), the following findings have been made: Hardcoded AES parameters (CVE-2018-5298) and twitter keys These parameters are stored in the class OralBApplication and also get used there: Using the twitter secrets, it's possible to create bearer tokens impersonating the Oral-B twitter application. The secrets stored in the app are application tokens only - in my tests it was not possible to authenticate in user context. The stored AES parameters are used to encrypt and decrypt the locally stored shared preferences in the class called Preferences : Because of the static key, an attacker can gain access to user data more easily by leveraging access to the preferences XML file. Tracking Upon running the app, the user automatically gets tracked. There is no opt-in required, it's enabled by default. As you can see, third party advertising providers are allowed to gain access to the us...